For security reasons, you can specify access settings for database users, in order to allow or deny remote connections to a database. Remote connections can be allowed from certain IP addresses. For example, if a script running on a remote host accesses a Plesk database by using the credentials of a certain database user, then you can restrict the access of this user to the IP address of that remote host.
Depending on the database server type, Plesk employs different tools for access control:
Note: Plesk adds new rules to the firewall only with your approval. Each time a subscriber sets up a custom access control rule, Plesk notifies you about this and prompts you to accept or reject the changes.
The access control options are available at Websites & Domains > Databases when you add or edit a database or a database user. For details, see the section Setting Up Custom Access Rules.
When a customer, a subscription, or a database user is removed, all associated firewall rules are removed too.
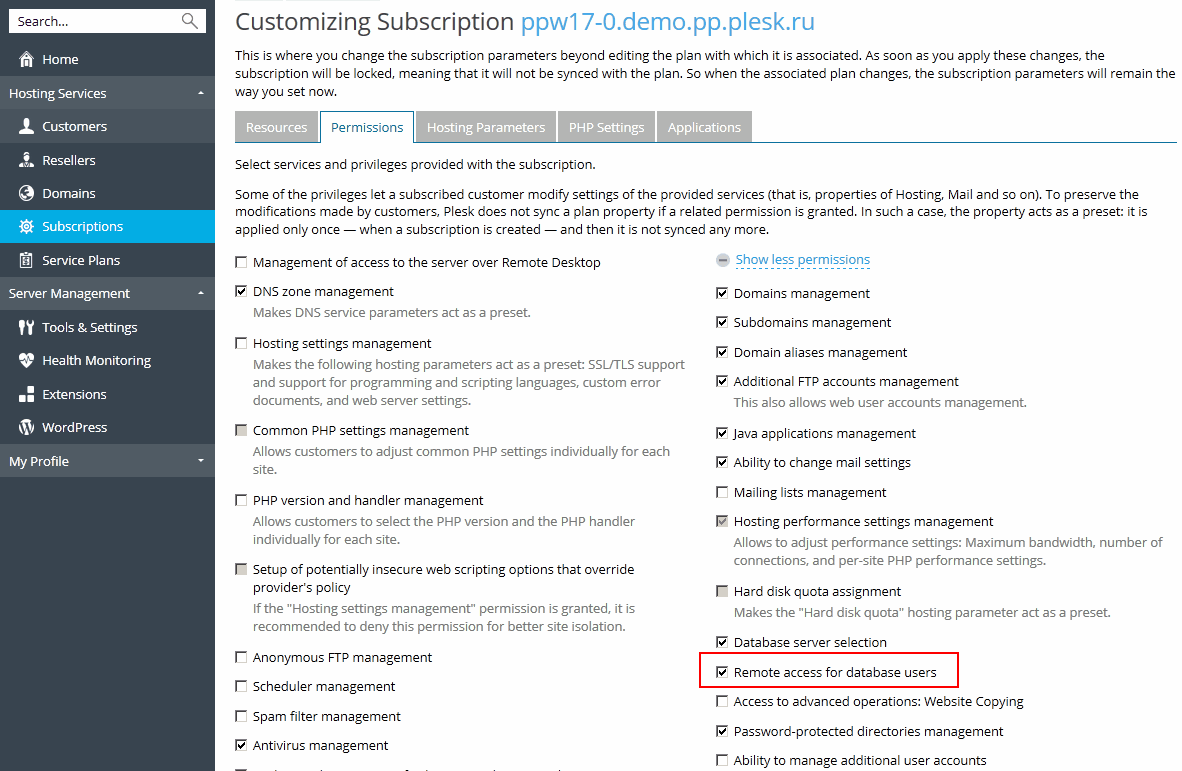
To enable subscribers to customize access to their databases:
After a user has specified custom rules, the Plesk administrator receives the following notification displayed on the Home page of the Server Administration Panel: Remote access rules for database users were modified and are waiting for your approval. Please go to Firewall Settings to review and confirm the rules.
After reviewing the rules, you should decide whether to confirm the addition of the custom rules to the set of system firewall rules. Use Apply Changes or Discard Changes buttons on the Plesk for Linux firewall rules page for not applied configurations (Firewall > Modify Plesk Firewall Rules).