HTTP/2 (also known as HTTP/2.0 and HTTP 2.0) is the second major version of the HTTP network protocol used by the World Wide Web. Ratified in May 2015, HTTP/2 was created to address some significant performance problems with HTTP 1.1. The advantages of this protocol can be found here. Currently HTTP/2 is supported by most major web browsers.
HTTP/2 support is available for Plesk customers starting from the version 12.5.30 Update #28 and requires the latest version of nginx.
Note: HTTP/2 is supported for SSL sites only, so non-SSL sites will continue to work under HTTP/1.x.
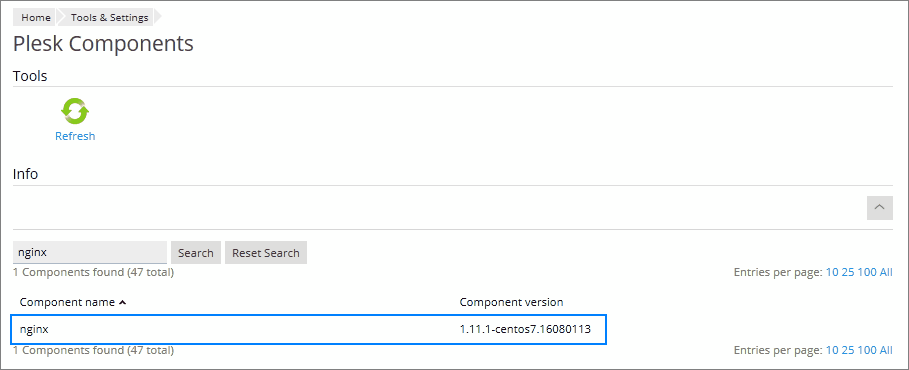
Make sure you have nginx web server updated to the latest version and running. You can do this on the Tools & Settings -> Server Components and the Tools & Settings -> Services Management pages.

Login to your server via SSH under root and enable HTTP/2 support in Plesk using the following command line utility:
# plesk bin http2_pref enable
During the last step your nginx web server will be tuned to use the TLS protocol with modern and secure ciphers, the whole web server configuration will be rebuilt, and all your and your customers’ web sites with SSL support will be moved to HTTP/2.
Please check the output of the command for errors or warnings during switching to HTTP/2. If there are any problems, refer to the Troubleshooting section below.
Note: You can simply use an online service like https://tools.keycdn.com/http2-test to check that HTTP/2 is enabled on a domain.
If you wish to return to HTTP 1.x and to disable HTTP/2, please use the following command:
# plesk bin http2_pref disable
For correct use of HTTP/2 in Google Chrome, nginx web server has to support the ALPN (Application-Layer Protocol Negotiation). For details, see the ALPN documentation.
ALPN support for nginx web server is available in Plesk for the following operating systems: CentOS 7, RedHat Enterprise Linux 7, Ubuntu 14.04, Ubuntu 16.04, and Debian 8.
This means that HTTP/2 powered by Plesk works on the mentioned operation systems in all modern browsers.
If you have trouble enabling HTTP/2 support for a web site, or the result of checking the site with https://tools.keycdn.com/http2-test shows only the HTTP 1.x protocol enabled, follow the steps below to troubleshoot this behavior.
# plesk sbin nginxmng –s
Enable it if necessary:
# plesk sbin nginxmng -e
# rpm -qa | grep openssl
openssl-1.0.1e-42.el6_7.4.x86_64.
/usr/local/psa/admin/conf/templates/custom/domain/nginxDomainVirtualHost.php. Remove it if it was found and re-create configuration files:# plesk sbin httpdmng --reconfigure-all
Alternatively, if you do not want to remove your customizations, you can modify the file /usr/local/psa/admin/conf/templates/custom/domain/nginxDomainVirtualHost.php like below.
Find the row similar to
($OPT['default'] ? ' default_server' : '') . ($OPT['ssl'] ? ' ssl' : '') ?>;
And replace it with the two following rows:
($OPT['default'] ? ' default_server' : '') . ($OPT['ssl'] ? ' ssl' : '') .
($OPT['ssl'] && $VAR->domain->physicalHosting->proxySettings['nginxHttp2'] ? ' http2' : '') ?>;
After that run the command:
# plesk bin http2_pref enable
ssl_ciphers directive in /etc/nginx/conf.d/ssl.conf or in customised nginxDomainVirtualHost.php has the following value: ssl_ciphers EECDH+AESGCM+AES128:EECDH+AESGCM+AES256:EECDH+CHACHA20:EDH+AESGCM+AES128:EDH+AESGCM+AES256:EDH+CHACHA20:EECDH+SHA256+AES128:EECDH+SHA384+AES256:EDH+SHA256+AES128:EDH+SHA256+AES256:EECDH+SHA1+AES128:EECDH+SHA1+AES256:EDH+SHA1+AES128:EDH+SHA1+AES256:EECDH+HIGH:EDH+HIGH:AESGCM+AES128:AESGCM+AES256:CHACHA20:SHA256+AES128:SHA256+AES256:SHA1+AES128:SHA1+AES256:HIGH:!aNULL:!eNULL:!EXPORT:!DES:!RC4:!MD5:!PSK:!KRB5:!aECDH:!EDH+3DES;
sslmng utility from Plesk to set up available protocols and TLS ciphers list after you have enabled HTTP/2. For example if you want to use exactly the same ciphers list as Plesk does, the command will be the following:#plesk sbin sslmng --services=nginx --custom --ciphers="EECDH+AESGCM+AES128:EECDH+AESGCM+AES256:EECDH+CHACHA20:EDH+AESGCM+AES128:EDH+AESGCM+AES256:EDH+CHACHA20" --protocols="TLSv1 TLSv1.1 TLSv1.2"
Configuration will be stored in the /etc/nginx/conf.d/ssl.conf file. We do not recommend to edit this file manually.