SSL/TLS certificates protect sensitive data by encrypting connections between the client and the server. Moreover, having a valid SSL/TLS certificate is practically a requirement on today's Internet. To improve security and give your customers peace of mind, we strongly recommend protecting Plesk and the Plesk mail server with SSL/TLS certificates. This topic explains how to secure both Plesk and the Plesk mail server with a free SSL/TLS certificate from Let's Encrypt, an SSL/TLS certificate purchased from a certificate authority, or a self-signed SSL/TLS certificate.
During installation, both Plesk and the Plesk mail server are automatically secured with a free self-signed SSL/TLS certificate. This allows for encrypting connections to Plesk and the Plesk mail server so that, for example, passwords could not be intercepted in transit. However, self-signed SSL/TLS certificates come with a drawback. Anyone visiting a Plesk server secured with a self-signed SSL/TLS certificate is shown a warning telling them that the website is not trusted, which may cause concern. To avoid this, we recommend securing Plesk and the Plesk mail server with either a free SSL/TLS certificate from Let's Encrypt or an SSL/TLS certificate purchased from a certificate authority.
Note: If you secure the Plesk mail server with an SSL/TLS certificate, make sure to use the domain name for which the certificate was issued when connecting to the mail server, and advise your customers to do the same. Otherwise, the mail client software may be unable to verify the mail server identity, which may cause issues when sending or receiving mail.
Let’s Encrypt is an open certificate authority providing free SSL/TLS certificates. You can easily secure both Plesk and the Plesk mail server with SSL/TLS certificates using the free Let’s Encrypt extension.
When you install or upgrade the Let’s Encrypt extension, if Plesk is secured with a self-signed certificate, the extension automatically replaces it with a valid SSL/TLS certificate from Let’s Encrypt. The extension does not automatically secure the Plesk mail server.
If you want to replace a valid certificate issued by a certificate authority with one from Let’s Encrypt, follow the steps below.
To secure Plesk and the mail server with a certificate from Let’s Encrypt:
At this stage, the certificate from Let’s Encrypt has been generated and used to secure Plesk automatically.
Now both Plesk and the Plesk mail server are secured with the certificate from Let’s Encrypt.
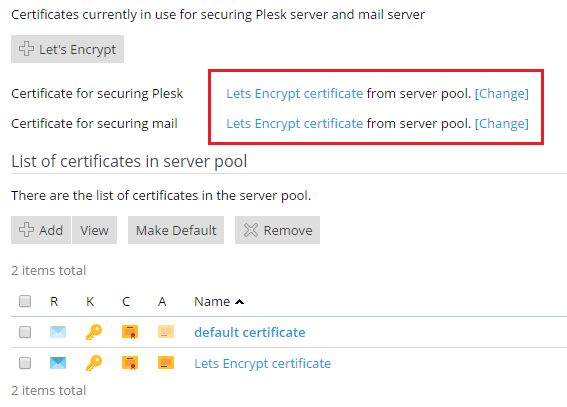
Note: In Plesk for Linux, when Let’s Encrypt replaces the default self-signed certificate, in Tools & Settings > SSL/TLS Certificates the name of the certificate used to secure Plesk is changed to “Lets Encrypt certificate”. In Plesk for Windows, the default certificate name is changed to “Lets Encrypt certificate” only after you reload the Tools & Settings > SSL/TLS Certificates web page in the browser.
Apart from Let’s Encrypt, you can secure Plesk and the Plesk mail server with an SSL/TLS certificate from a certificate authority of your choice.
To secure Plesk and the mail server with a certificate from other certificate authorities:
Plesk will generate a private key and a certificate signing request and display them in under “List of certificates in server pool”.
Copy the whole content of the “CSR” section (including -----BEGIN CERTIFICATE REQUEST----- and -----END CERTIFICATE REQUEST-----) to clipboard.
.crt file, and then click Upload Certificate. As we explained earlier, self-signed SSL/TLS certificates are never trusted. It is always preferable to use an SSL/TLS certificate from Let's Encrypt or a paid SSL/TLS certificate from a different certificate authority. However, you can secure Plesk and the mail server with a self-signed SSL/TLS certificate, if desired.
To secure Plesk and the mail server with a self-signed certificate: