If your hosting offerings include mail services, keep in mind that your mail server can be used for malicious purposes, such as sending spam. Outgoing spam can cause an increased load on the server and complaints from recipients. What’s more important, your server IP addresses might be added to public black lists, such as Spamhaus or OpenBL lists.
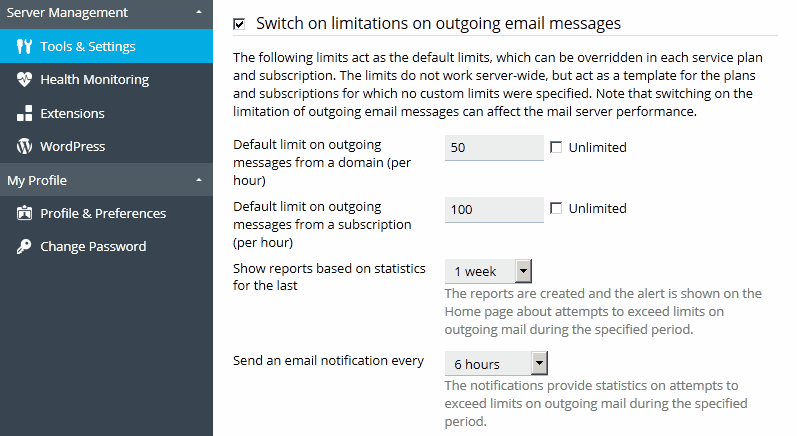
To prevent spam being sent from your server, Plesk offers a tool that controls the sending of email messages. This tool gathers statistics about outgoing messages and prevents mail being sent when specified limits are exceeded. You can specify limits on outgoing mail at the following levels: mail server, service plan, subscription, domain, and mailbox.
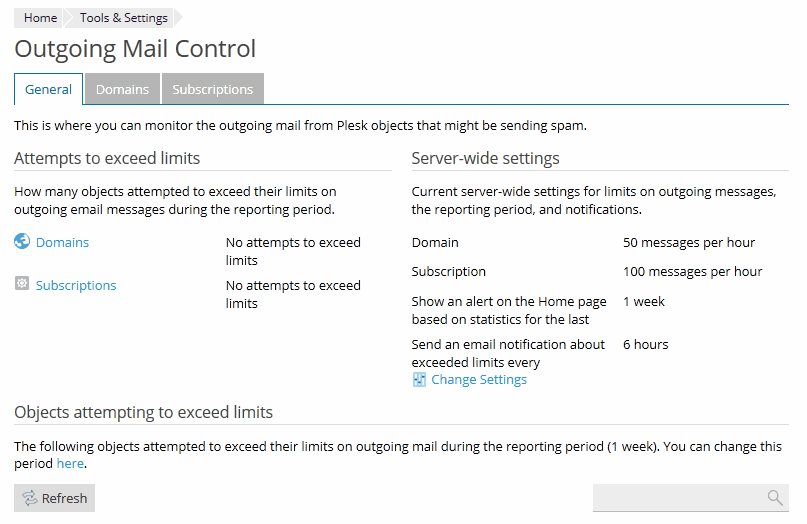
Administrators can prevent outgoing spam by using limits on the number of outgoing email messages per hour. In addition, the administrator can easily determine the exact source of possible spam with the help of reports and notifications.
Plesk introduces different limits for prevention of the following different types of threats:
SMTP user account credentials can be stolen by malicious users when they hack a mail server by using a system vulnerability (for example, PHP vulnerability) or an application exploit (for example, exploit for an outdated WordPress version). Also, if customers use very weak passwords, their passwords can be obtained by using brute force tools.
You can prevent this type of threat by limiting the number of outgoing email messages from a mailbox.
A malicious user can use a Plesk customer account in order to create a website with a script that will distribute spam emails. Also, a malicious user can steal the FTP credentials of a customer account and upload a website with a mass mailing script via FTP.
You can prevent this type of threat by limiting the number of outgoing email messages from a domain.
Malicious users can gain access to Linux system user accounts by using system or application exploits. After that, they can plant scheduled background tasks in crontab. Such scheduled tasks can run mass mailing scripts that spread spam mail.
You can prevent this type of threat by limiting the number of outgoing email messages from a subscription.
To protect against spam by limiting outgoing mail, follow the steps:
Note: Starting with Plesk 12, the 127.0.0.0/8 network is no longer added to the whitelist by default. This is necessary for outbound spam protection to function correctly. Not having localhost whitelisted prevents PHP scripts from sending mail on Windows. Other scripting engines may be affected as well. Also, Mailman will not be able to send emails to external email addresses.
Note: The Outgoing Mail Control link is displayed only if the limitations are switched on in the mail server settings.
Some kinds of outgoing messages cannot be counted in Outgoing Mail Control due to mail server or mailing lists software restrictions. This might lead to Plesk not blocking excessive outgoing mail. Therefore, be aware of the limitations in the following areas:
Protection from Outbound Spam |
Linux |
Windows |
||
All mail servers supported by Plesk |
MailEnable |
SmarterMail |
IceWarp |
|
Limiting outgoing mail for a mailbox |
Yes |
No |
Yes |
No |
Limiting outgoing mail for a domain |
Yes |
Yes |
Yes |
No |
Limiting outgoing mail for a subscription |
Yes |
Yes |
No |
No |
Tracking of mail sent by scripts |
Yes |
No |
No |
No |
Mail Forwarding to Mailboxes on Local or Remote Servers |
Linux |
Windows |
||
All mail servers supported by Plesk |
MailEnable |
SmarterMail |
IceWarp |
|
Forwarded messages to local recipients are counted |
Yes |
No |
No |
No |
Forwarded messages to remote recipients are counted |
Yes |
No |
Yes |
No |